smart card is an example of which type of authentication Smart cards serve as credit or ATM cards, fuel cards, mobile phone SIMs, authorization cards for pay television, household utility pre-payment cards, high-security identification and access badges, and public transport and public phone payment cards. Smart cards may also be used as electronic wallets. The smart card chip can . QUICK ANSWER. NFC tags and readers communicate wirelessly with each other over very short distances. Tags store a small amount of data on them that is sent to the reader in the form of .
0 · windows 10 smart card setup
1 · what is smart card authentication
2 · what is an example of two factor authentication 2fa
3 · what is an example of a logical access control
4 · true or false a smart card is an example of a logical access control
5 · smart card based authentication
6 · smart card authentication step by
7 · authenticate using your smart card
Using a Desktop NFC Reader and Writer to program, edit, or read NFC cards, tags, and more. .
windows 10 smart card setup
Smart cards serve as credit or ATM cards, fuel cards, mobile phone SIMs, authorization cards for pay television, household utility pre-payment cards, high-security identification and access badges, and public transport and public phone payment cards. Smart cards may also be used as electronic wallets. The smart card chip can . Smart card authentication is a method that employs the embedded chip in the card to verify the identity of the user certificates. The chip can generate or store authentication data .

m24sr64 nfc rfid tag ic
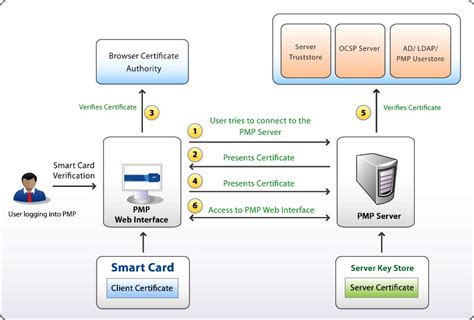
Smart Card Authentication is a means of verifying users into enterprise resources such as workstations and applications using a physical card in tandem with a smart card reader and .Organizations also use them for security purposes, as MFA tokens and for authenticating single sign-on users and enabling passwordless authentication. Types of smart cards. Smart cards are categorized based on criteria such as . Something you have (such as a smart card) Something you are (such as a fingerprint or other biometric method) Identification occurs when a user professes an identity .
There are generally three types of smart cards: contact cards, contactless cards, and hybrid cards. Contact intelligent cards require physical contact with a reader to function. They are commonly used in ATM . In this article we have covered the basics of Certificate-Based Authentication (CBA) using a smart card or a YubiKey (as a smart card). We have learned that CBA uses a certificate describing the user and that this certificate .
Certificate-based authentication is an encrypted method that enables devices and people to identify themselves to other devices and systems. Two common examples are a smart card or .Smart cards, occasionally called chip cards or integrated circuit cards (IC or ICC), are a broad family of physical electronic authentication devices. More practically, they’re physically-secured microprocessors used to control access to resources.Different types of smart cards, from left to right: online authentication access (with the US DoD smart badge - military CAC), secure transaction with an EMV card (with a biometric sensor), strong identification with your national ID card. What are the types of smart cards? To begin with, magnetic stripe cards are definitively not smart cards.
Smart cards serve as credit or ATM cards, fuel cards, mobile phone SIMs, authorization cards for pay television, household utility pre-payment cards, high-security identification and access badges, and public transport and public phone payment cards. Smart card authentication is a method that employs the embedded chip in the card to verify the identity of the user certificates. The chip can generate or store authentication data through cryptographic algorithms that a reader can verify.Smart Card Authentication is a means of verifying users into enterprise resources such as workstations and applications using a physical card in tandem with a smart card reader and software on the workstation.Organizations also use them for security purposes, as MFA tokens and for authenticating single sign-on users and enabling passwordless authentication. Types of smart cards. Smart cards are categorized based on criteria such as how the card reads and writes data, the type of chip used and its capabilities. They include the following types:
Something you have (such as a smart card) Something you are (such as a fingerprint or other biometric method) Identification occurs when a user professes an identity (such as with a username), and authentication occurs when users prove their identity. For example, users are authenticated when they provide both their username and correct password. There are generally three types of smart cards: contact cards, contactless cards, and hybrid cards. Contact intelligent cards require physical contact with a reader to function. They are commonly used in ATM transactions, secure computer logins, and point-of-sale systems. In this article we have covered the basics of Certificate-Based Authentication (CBA) using a smart card or a YubiKey (as a smart card). We have learned that CBA uses a certificate describing the user and that this certificate bundles a public key.Certificate-based authentication is an encrypted method that enables devices and people to identify themselves to other devices and systems. Two common examples are a smart card or when an employee’s device sends a digital certificate to a network or server.
Smart cards, occasionally called chip cards or integrated circuit cards (IC or ICC), are a broad family of physical electronic authentication devices. More practically, they’re physically-secured microprocessors used to control access to resources.Different types of smart cards, from left to right: online authentication access (with the US DoD smart badge - military CAC), secure transaction with an EMV card (with a biometric sensor), strong identification with your national ID card. What are the types of smart cards? To begin with, magnetic stripe cards are definitively not smart cards.Smart cards serve as credit or ATM cards, fuel cards, mobile phone SIMs, authorization cards for pay television, household utility pre-payment cards, high-security identification and access badges, and public transport and public phone payment cards.
Smart card authentication is a method that employs the embedded chip in the card to verify the identity of the user certificates. The chip can generate or store authentication data through cryptographic algorithms that a reader can verify.Smart Card Authentication is a means of verifying users into enterprise resources such as workstations and applications using a physical card in tandem with a smart card reader and software on the workstation.Organizations also use them for security purposes, as MFA tokens and for authenticating single sign-on users and enabling passwordless authentication. Types of smart cards. Smart cards are categorized based on criteria such as how the card reads and writes data, the type of chip used and its capabilities. They include the following types: Something you have (such as a smart card) Something you are (such as a fingerprint or other biometric method) Identification occurs when a user professes an identity (such as with a username), and authentication occurs when users prove their identity. For example, users are authenticated when they provide both their username and correct password.
There are generally three types of smart cards: contact cards, contactless cards, and hybrid cards. Contact intelligent cards require physical contact with a reader to function. They are commonly used in ATM transactions, secure computer logins, and point-of-sale systems. In this article we have covered the basics of Certificate-Based Authentication (CBA) using a smart card or a YubiKey (as a smart card). We have learned that CBA uses a certificate describing the user and that this certificate bundles a public key.Certificate-based authentication is an encrypted method that enables devices and people to identify themselves to other devices and systems. Two common examples are a smart card or when an employee’s device sends a digital certificate to a network or server.
what is smart card authentication
what is an example of two factor authentication 2fa
longest range nfc tag
what is an example of a logical access control
An NFC tag reader is a device that can read an NFC tag. In most cases, it will provide power to the NFC tag that it’s reading. There are billions of NFC readers out there in the world; in fact .NFC tags are passive, meaning they don't have any power source. Instead, they literally draw power from the device that reads them, thanks to .
smart card is an example of which type of authentication|windows 10 smart card setup