rfid track is something stolen Radio-Frequency Identification (RFID) involves the use of radio waves to read and capture information stored on an electronic chip attached to an object. RFID chips, or “tags,” can be read via scanning devices from up to several feet away. These chips have been used by businesses for years to manage inventory . See more Check out our nfc tags business cards selection for the very best in unique or .
0 · what does rfid theft mean
1 · rfid theft hack
2 · rfid theft
3 · how to stop rfid theft
4 · how do you steal rfid
5 · how do rfid thefts work
6 · how do rfid thefts happen
7 · credit card rfid theft
The ones up for grabs include the new Link amiibo from Tears of the Kingdom and the Breath of the Wild Bokoblin (thanks, Amiibo . The NFC .
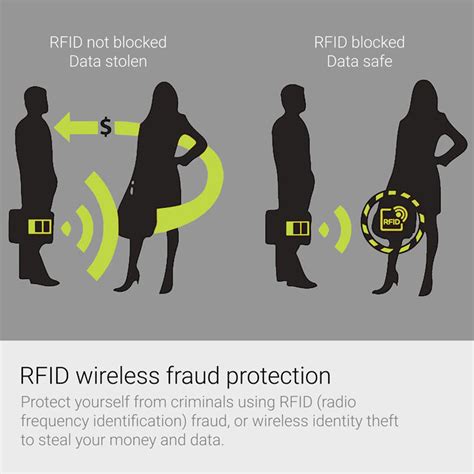
Radio-Frequency Identification (RFID) involves the use of radio waves to read and capture information stored on an electronic chip attached to an object. RFID chips, or “tags,” can be read via scanning devices from up to several feet away. These chips have been used by businesses for years to manage inventory . See moreSome security experts have voiced concerns about a phenomenon called RFID skimming, in which a thief with an RFID reader may be able to steal your credit card number or personal information simply by walking within a few feet of you. It’s a scary thought, . See moreWhile RFID skimming should be the least of your worries, it’s important to take steps to protect against the very real threats of credit card fraud and other forms of identity theft. Be proactive with automatic, 24/7 monitoring of your credit report and credit score, so you’ll . See more It does not allow retailers to broadly track a customers' whereabouts if they are wearing the clothes and cannot even help track items .
You probably know that the embedded computer chips found in most credit and debit cards are meant to protect you from financial fraud. But you may have also heard of a . It does not allow retailers to broadly track a customers' whereabouts if they are wearing the clothes and cannot even help track items if they’re stolen or lost. Instead, RFID . RFID theft occurs when someone uses their own RFID reader to trigger the chip in your credit card; a process called ‘skimming’ or ‘digital pickpocketing.’ The card thinks it is . RFID theft, also known as skimming or electronic pickpocketing, involves the unauthorized access and theft of personal information stored on RFID-enabled cards or tags. .
Learn how to prevent RFID hacking with our comprehensive guide. Increase your business safety and convenience while eliminating RFID attacks. Click here!Wireless identity theft, also known as contactless identity theft or RFID identity theft, is a form of identity theft described as "the act of compromising an individual’s personal identifying . Be sure to check your original account to make sure no money has been stolen. Check your accounts. If personal information has been compromised, thieves may try to . RFID gives retailers crime fighting capabilities they have wanted for decades, says the Managing Director of the Loss Prevention Research Council.
While the technology is limited, these tiny RFID tags allow retailers to track when inventory goes missing, which helps alert store managers to a potential theft, he said. For retailers, using RFID readers at all exit locations can trigger an alarm if someone tries to slip out the door with stolen goods. Electronic article surveillance (EAS) . You probably know that the embedded computer chips found in most credit and debit cards are meant to protect you from financial fraud. But you may have also heard of a .
It does not allow retailers to broadly track a customers' whereabouts if they are wearing the clothes and cannot even help track items if they’re stolen or lost. Instead, RFID .
what does rfid theft mean
RFID theft occurs when someone uses their own RFID reader to trigger the chip in your credit card; a process called ‘skimming’ or ‘digital pickpocketing.’ The card thinks it is . RFID theft, also known as skimming or electronic pickpocketing, involves the unauthorized access and theft of personal information stored on RFID-enabled cards or tags. . Learn how to prevent RFID hacking with our comprehensive guide. Increase your business safety and convenience while eliminating RFID attacks. Click here!
Wireless identity theft, also known as contactless identity theft or RFID identity theft, is a form of identity theft described as "the act of compromising an individual’s personal identifying . Be sure to check your original account to make sure no money has been stolen. Check your accounts. If personal information has been compromised, thieves may try to . RFID gives retailers crime fighting capabilities they have wanted for decades, says the Managing Director of the Loss Prevention Research Council. While the technology is limited, these tiny RFID tags allow retailers to track when inventory goes missing, which helps alert store managers to a potential theft, he said.
rfid theft hack
rfid theft
how to stop rfid theft
3. Insert smart card into the ACR1255U-J1 reader. 4. In the demo application on the mobile device, tap Script File, and then locate the .txt file to run. Page 23 6. The Escape Response will be displayed as part of the logs. Page 23 of 48 .
rfid track is something stolen|how do you steal rfid