add encrypted smart cards Insert your PIV card in your computer’s smart card reader. Browse to File > Options > Trust Center > Trust Center Settings and select Email Security. Click Publish to GAL. beneath the Digital IDs (Certificates) heading. Click OK when warned about Outlook publishing your default security certificates to the Global Address List.
Listen online to ESPN 106.7 radio station for free – great choice for Auburn, United States. Listen live ESPN 106.7 radio with Onlineradiobox.com . Opelika, with the call-sign WGZZ-HD3, is a sports-format radio station serving Auburn .
0 · Understanding Smart Card Authentication
1 · Personal Identity Verification Card 101
2 · Get Started with Virtual Smart Cards
This is how I think the radio announcers looked when the "Kick 6" took place

By utilizing Trusted Platform Module (TPM) devices that provide the same cryptographic capabilities as physical smart cards, virtual smart cards accomplish the three . Virtual smart cards that utilize a TPM provide the three main security principles of traditional smart cards: nonexportability, isolated cryptography, and anti-hammering. Virtual smart cards are less expensive to implement and more convenient for users. By utilizing Trusted Platform Module (TPM) devices that provide the same cryptographic capabilities as physical smart cards, virtual smart cards accomplish the three key properties that are desired by smart cards: nonexportability, isolated cryptography, and .
Virtual smart cards are functionally similar to physical smart cards, appearing in Windows as smart cards that are always-inserted. Virtual smart cards can be used for authentication to external resources, protection of data by . In this article we have covered the basics of Certificate-Based Authentication (CBA) using a smart card or a YubiKey (as a smart card). We have learned that CBA uses a certificate describing the user and that this certificate bundles a public key.Insert your PIV card in your computer’s smart card reader. Browse to File > Options > Trust Center > Trust Center Settings and select Email Security. Click Publish to GAL. beneath the Digital IDs (Certificates) heading. Click OK when warned about Outlook publishing your default security certificates to the Global Address List. Step-by-step demonstration of how to use a smart card in conjunction with Microsoft's BitLocker data encryption solution. More info can be found here http://.
This guide provides steps to configure a BitLocker encrypted drive that can be unlocked with a YubiKey 5 series device in Smart Card mode. This will result in a BitLocker drive that is secured by a physical piece of hardware and .
Understanding Smart Card Authentication
Virtual smart cards with Windows 10 are a great way to increase sign-in security without additional costs and extra hardware attached to end user PCs. If you have a TPM installed and your machine is encrypted, it simply involves creating the certificate template, creating the virtual smart card, and then issuing the VSC template to the end user. You can use smart card certificates with BitLocker Drive Encryption to protect fixed and removable data drives and to recover BitLocker-protected drives in the absence of the primary access key. Once you have obtained certificates, you can use them with BitLocker data recovery agents and as a BitLocker key protector for data drives. I'd like to use my YubiKey 5 NFC as a Smart Card to unlock a BitLocker-protected drive. I went into the Manage BitLocker Control Panel and clicked "Add smart card" but got two errors (screenshots here ). Virtual smart cards that utilize a TPM provide the three main security principles of traditional smart cards: nonexportability, isolated cryptography, and anti-hammering. Virtual smart cards are less expensive to implement and more convenient for users.
By utilizing Trusted Platform Module (TPM) devices that provide the same cryptographic capabilities as physical smart cards, virtual smart cards accomplish the three key properties that are desired by smart cards: nonexportability, isolated cryptography, and .
Personal Identity Verification Card 101
Virtual smart cards are functionally similar to physical smart cards, appearing in Windows as smart cards that are always-inserted. Virtual smart cards can be used for authentication to external resources, protection of data by . In this article we have covered the basics of Certificate-Based Authentication (CBA) using a smart card or a YubiKey (as a smart card). We have learned that CBA uses a certificate describing the user and that this certificate bundles a public key.
Insert your PIV card in your computer’s smart card reader. Browse to File > Options > Trust Center > Trust Center Settings and select Email Security. Click Publish to GAL. beneath the Digital IDs (Certificates) heading. Click OK when warned about Outlook publishing your default security certificates to the Global Address List.
Step-by-step demonstration of how to use a smart card in conjunction with Microsoft's BitLocker data encryption solution. More info can be found here http://. This guide provides steps to configure a BitLocker encrypted drive that can be unlocked with a YubiKey 5 series device in Smart Card mode. This will result in a BitLocker drive that is secured by a physical piece of hardware and .
Virtual smart cards with Windows 10 are a great way to increase sign-in security without additional costs and extra hardware attached to end user PCs. If you have a TPM installed and your machine is encrypted, it simply involves creating the certificate template, creating the virtual smart card, and then issuing the VSC template to the end user. You can use smart card certificates with BitLocker Drive Encryption to protect fixed and removable data drives and to recover BitLocker-protected drives in the absence of the primary access key. Once you have obtained certificates, you can use them with BitLocker data recovery agents and as a BitLocker key protector for data drives.
harber london leather bifold wallet with rfid protection
is rfid protection needed
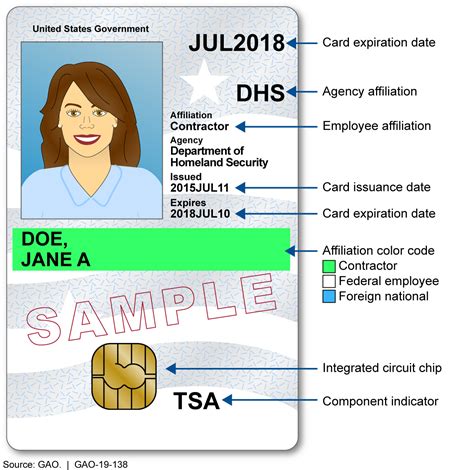
Get Started with Virtual Smart Cards
TIGER TALK. Thursdays at 6 p.m. CT. Hosted by Brad Law and the Voice of the Tigers, Andy Burcham, weekly guests will include head football coach Hugh Freeze in the fall .
add encrypted smart cards|Understanding Smart Card Authentication