bitlocker virtual smart card By utilizing Trusted Platform Module (TPM) devices that provide the same . Yes, all types of amiibo and amiibo cards are reusable. No amiibo are destroyed when in use. However, amiibo chips don’t last forever, so you shouldn’t scan them dozens of times a day for fun. . So as Amiibo NFC tag .
0 · smart card to unlock bitlocker
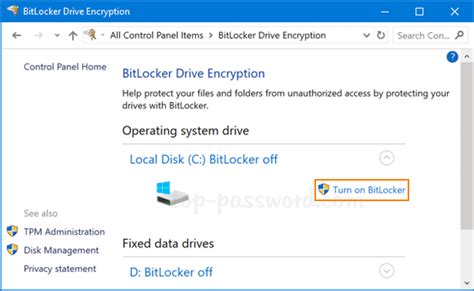
1 · is bitlocker turned on
2 · how to implement bitlocker
3 · how to bitlocker a drive
4 · enable bitlocker on drive
5 · enable bitlocker in windows 10
6 · bitlocker smart card windows 11
7 · bitlocker smart card windows 10
Get it here - https://amzn.to/457EyhgLink to my amazon store - .
smart card to unlock bitlocker
Virtual smart cards are functionally similar to physical smart cards, appearing in Windows as smart cards that are always-inserted. Virtual smart cards can be used . See moreTo use the virtual smart card technology, TPM 1.2 is the minimum required for devices running a supported operating system. See more By utilizing Trusted Platform Module (TPM) devices that provide the same .
Customers using virtual smart cards are encouraged to move to Windows Hello .
This is my first blog and today I’ll share with you how to configure a Hyper-V .
This guide provides steps to configure a BitLocker encrypted drive that can be unlocked with a YubiKey 5 series device in Smart Card mode. This will result in a BitLocker drive that is secured by a physical piece of hardware . Virtual smart cards can be used in domain-joined Windows 10 devices equipped with a TPM (version 1.2 or version 2.0). In addition, they require an accessible PKI infrastructure in the environment, such as Microsoft . Virtual smart cards are functionally similar to physical smart cards, appearing in Windows as smart cards that are always-inserted. Virtual smart cards can be used for authentication to external resources, protection of data by .
By utilizing Trusted Platform Module (TPM) devices that provide the same cryptographic capabilities as physical smart cards, virtual smart cards accomplish the three key properties that are desired by smart cards: nonexportability, isolated cryptography, and .
Customers using virtual smart cards are encouraged to move to Windows Hello for Business or FIDO2. For new Windows installations, we recommend Windows Hello for Business or FIDO2 security keys. Learn about the requirements for . This is my first blog and today I’ll share with you how to configure a Hyper-V environment in order to enable virtual smart card logon to VM guests by leveraging a new Windows 10 feature: virtual Trusted Platform Module (TPM).
This guide provides steps to configure a BitLocker encrypted drive that can be unlocked with a YubiKey 5 series device in Smart Card mode. This will result in a BitLocker drive that is secured by a physical piece of hardware and . Virtual smart cards can be used in domain-joined Windows 10 devices equipped with a TPM (version 1.2 or version 2.0). In addition, they require an accessible PKI infrastructure in the environment, such as Microsoft Certificate Services. The basic process of using virtual smart cards involves three steps: This article describes the virtual smart card technology and how it can fit into your authentication design. Virtual smart card technology uses cryptographic keys that are stored on computers that have the Trusted Platform Module (TPM) installed. Trying to have a good overview about the security of Virtual Smart Cards relying on TPMs, I read this very short article (the only I found) covering this topic (first part): https://docs.microsoft.com/en-us/windows/security/identity-protection/virtual-smart-cards/virtual-smart-card-evaluate-security. My understanding.
It describes three techniques for overcoming ARM TrustZone’s shortcomings: (1) provisioning additional trusted hardware, (2) making design compromises that do not affect TPM’s security, and (3) slightly changing the semantics of a small number of TPM 2.0 commands to adapt them to the TrustZone’s limitations.Virtual smart card technology offers comparable security benefits to physical smart cards by using two-factor authentication. Virtual smart cards emulate the functionality of physical smart cards, but they use the Trusted Platform Module (TPM) chip that is available on devices.

is bitlocker turned on
Virtual smart cards are functionally similar to physical smart cards, appearing in Windows as smart cards that are always-inserted. Virtual smart cards can be used for authentication to external resources, protection of data by . By utilizing Trusted Platform Module (TPM) devices that provide the same cryptographic capabilities as physical smart cards, virtual smart cards accomplish the three key properties that are desired by smart cards: nonexportability, isolated cryptography, and . Customers using virtual smart cards are encouraged to move to Windows Hello for Business or FIDO2. For new Windows installations, we recommend Windows Hello for Business or FIDO2 security keys. Learn about the requirements for . This is my first blog and today I’ll share with you how to configure a Hyper-V environment in order to enable virtual smart card logon to VM guests by leveraging a new Windows 10 feature: virtual Trusted Platform Module (TPM).
This guide provides steps to configure a BitLocker encrypted drive that can be unlocked with a YubiKey 5 series device in Smart Card mode. This will result in a BitLocker drive that is secured by a physical piece of hardware and .
Virtual smart cards can be used in domain-joined Windows 10 devices equipped with a TPM (version 1.2 or version 2.0). In addition, they require an accessible PKI infrastructure in the environment, such as Microsoft Certificate Services. The basic process of using virtual smart cards involves three steps: This article describes the virtual smart card technology and how it can fit into your authentication design. Virtual smart card technology uses cryptographic keys that are stored on computers that have the Trusted Platform Module (TPM) installed. Trying to have a good overview about the security of Virtual Smart Cards relying on TPMs, I read this very short article (the only I found) covering this topic (first part): https://docs.microsoft.com/en-us/windows/security/identity-protection/virtual-smart-cards/virtual-smart-card-evaluate-security. My understanding.It describes three techniques for overcoming ARM TrustZone’s shortcomings: (1) provisioning additional trusted hardware, (2) making design compromises that do not affect TPM’s security, and (3) slightly changing the semantics of a small number of TPM 2.0 commands to adapt them to the TrustZone’s limitations.
rfid 行业从业者,现在越来越多的企业会使用rfid,诚然,rfid的标签和使用成本是远高于条码的。 1,电子标签本身的价格是远高于条码标签的。 2,手持设备,虽然现在基本上,手持RFID读取器都是采用安卓的,但成本上还是高于条码手持读取器的。
bitlocker virtual smart card|how to implement bitlocker